考点:base64
靶机链接:https://www.vulnhub.com/entry/cybersploit-1,506/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.24 |
| CYBERSPLOIT-1 | 10.0.2.41 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
| $ export rip=10.0.2.41
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 01:1b:c8:fe:18:71:28:60:84:6a:9f:30:35:11:66:3d (DSA)
| 2048 d9:53:14:a3:7f:99:51:40:3f:49:ef:ef:7f:8b:35:de (RSA)
|_ 256 ef:43:5b:d0:c0:eb:ee:3e:76:61:5c:6d:ce:15:fe:7e (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Hello Pentester!
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
|_http-server-header: Apache/2.2.22 (Ubuntu)
|
WEB测试
dirsearch
1
2
3
4
5
6
7
| $ dirsearch -u http://10.0.2.41
[11:37:34] 403 - 285B - /cgi-bin/
[11:37:39] 200 - 2KB - /index.html
[11:37:39] 200 - 2KB - /index
[11:37:46] 200 - 79B - /robots.txt
[11:37:46] 403 - 290B - /server-status
[11:37:46] 403 - 291B - /server-status/
|
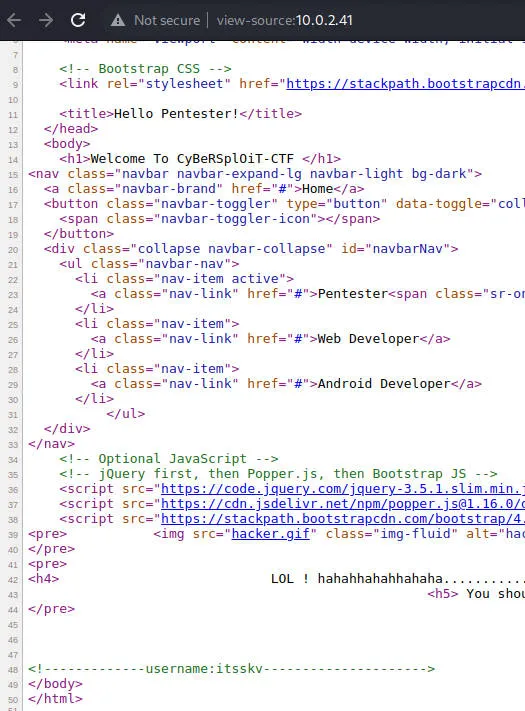
发现用户名itsskv
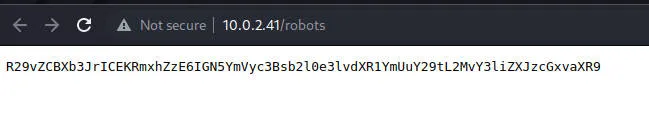
发现字符串R29vZCBXb3JrICEKRmxhZzE6IGN5YmVyc3Bsb2l0e3lvdXR1YmUuY29tL2MvY3liZXJzcGxvaXR9
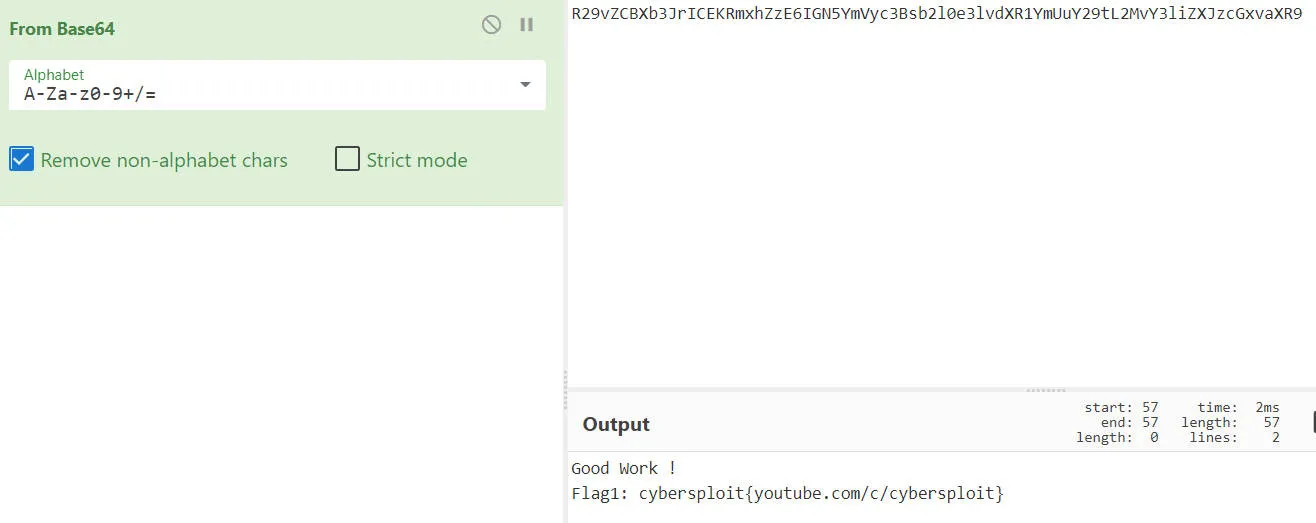
解密后
Good Work !
Flag1: cybersploit{youtube.com/c/cybersploit}
获得权限
用户itsskv 密码 cybersploit{youtube.com/c/cybersploit}
登录成功
提权
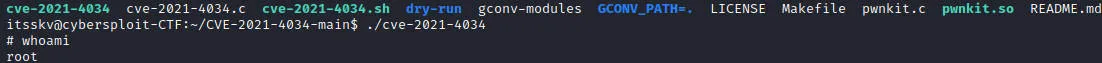
使用CVE-2021-4034 poc提权成功
最后修改于 2020-07-09



